Photo Credit: AQ’s Corner LLC
While reviewing my website logs, I noticed repeated requests resolving to North Bergen, New Jersey. What caught my attention was not that a location appeared, but that the location itself did not clearly explain what was happening.
North Bergen is not a place most people associate with identifiable online behavior. It does not register the way major cities do, and it did not point to a recognizable user pattern or platform. The label felt generic and low resolution, which made it difficult to immediately interpret what kind of traffic I was seeing.
That ambiguity is what prompted me to take a closer look.
When website activity points to a well known service or a familiar technical pattern, it is usually easy to understand what is happening. When it points to a generalized place name that does not clearly map to human behavior, the more useful question is not who is behind it, but what type of system would surface this way.
After digging further, it became clear that this activity was not human at all. It was routine internet infrastructure behavior.
Why Website Activity Often Resolves to Vague Locations
Every request to a website originates from an IP address. IP addresses do not identify people. They identify network infrastructure. Geolocation tools attempt to associate those addresses with physical locations, but the results are often approximate rather than precise.
When logs display a location such as North Bergen, New Jersey, they are not describing where a person is physically located. They are reflecting how internet infrastructure is registered and routed. Large blocks of IP addresses are often associated with nearby municipalities rather than specific facilities, which results in location labels that feel concrete but lack meaningful detail.
This lack of precision is not a flaw. It is a normal characteristic of IP based location data.
A Quick Lesson and Reminder on Data Centers
The internet does not exist solely in the cloud. It relies on physical buildings called data centers. These facilities house servers that store data, route traffic, cache content, and keep websites accessible.
Data centers tend to cluster in specific regions based on factors such as power availability, cooling capacity, network connectivity, and proximity to major population centers. Over time, this creates infrastructure dense corridors where enormous volumes of traffic pass through every day.
When website traffic resolves to a location that does not feel personal or recognizable, it is often because the traffic passed through one of these regions. IP geolocation tools then assign a nearby municipality as a reference point. The location reflects infrastructure, not user intent.
Why Places Like North Bergen Appear in Logs
The broader New York and New Jersey metro area is one of the most heavily trafficked internet regions in the United States. This is due to long-standing telecommunications infrastructure, proximity to major population centers, and the presence of numerous internet exchange points and regional network hubs.
Data centers, routing infrastructure, and network points of presence are distributed throughout the region, but IP geolocation does not map traffic to specific buildings or facilities. Instead, it relies on registration data, routing information, and regional attribution maintained by internet service providers and geolocation databases.
As a result, IP addresses are often associated with nearby municipalities or metropolitan areas rather than the exact location where traffic is processed. This is why website activity frequently resolves to places like North Bergen. It does not mean users are physically located there. It indicates that network infrastructure in the region is involved in handling or routing the traffic.
Over time, certain regions begin to appear repeatedly in website logs. Northern Virginia, parts of New Jersey, Silicon Valley, Dallas, Chicago, Atlanta, and Phoenix are common examples. These locations function as major routing and aggregation points in the physical backbone of the internet rather than destinations tied to individual users.
When Automation Is Mistaken for Human Activity
A significant portion of website traffic is automated. Search engines index content. Caches refresh pages. Monitoring tools check availability. Security scanners test for known vulnerabilities. Social platforms generate previews. Analytics systems collect metadata.
Most of this activity resolves to infrastructure locations rather than to individuals. Without context, it can feel personal. With context, it becomes predictable and routine.
Understanding this distinction helps prevent misinterpretation and unnecessary concern.
Why This Understanding Matters
The importance of understanding how infrastructure appears in logs is practical, not theoretical. When vague geographic signals are misread as human behavior, they can lead to incorrect assumptions or disproportionate responses.
When interpreted correctly, these signals provide useful information without alarm. Clarity allows website owners to distinguish normal background activity from behavior that genuinely warrants attention.
The Bigger Takeaway
Internet activity always resolves somewhere. That location, however, does not automatically imply intent, presence, or surveillance.
Once you understand how physical infrastructure surfaces in digital systems, ambiguity becomes informative rather than unsettling. Logs stop feeling personal and start functioning as what they are meant to be: technical signals.
That shift from reacting to data to understanding it is a core part of digital literacy.
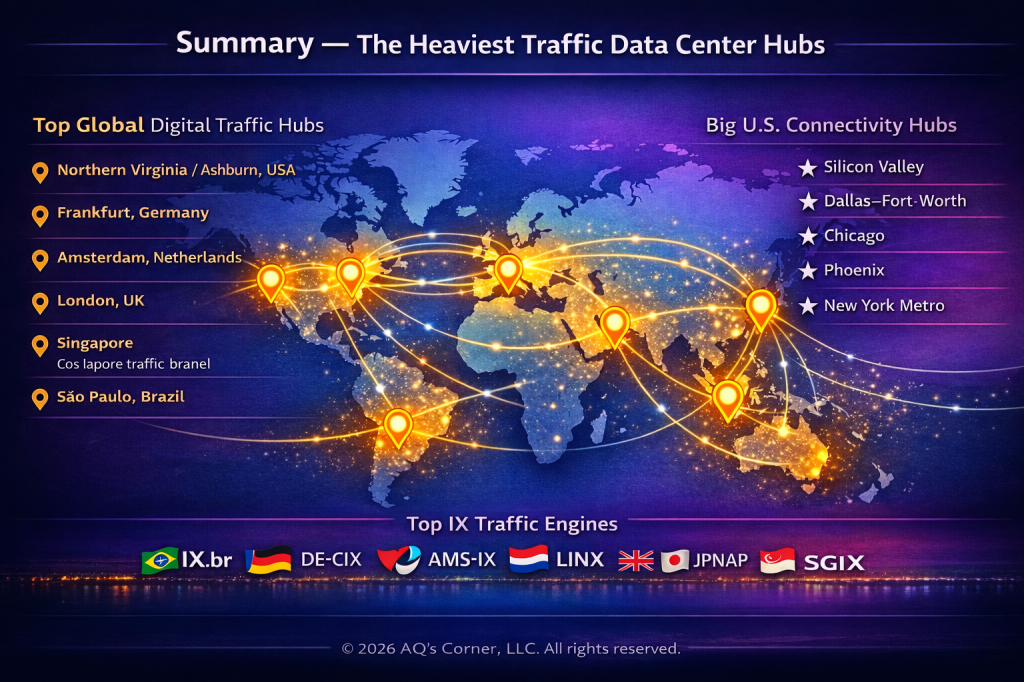
Summary: The Heaviest Traffic Data Center Hubs
This illustration highlights where global internet traffic actually concentrates, not around individual users, but around shared infrastructure that quietly moves data across regions and continents.
Top Global Digital Traffic Hubs
- Northern Virginia / Ashburn, USA
- Frankfurt, Germany
- Amsterdam, Netherlands
- London, United Kingdom
- Singapore
- São Paulo, Brazil
Big U.S. Connectivity Hubs
- Silicon Valley
- Dallas–Fort Worth
- Chicago
- Phoenix
- New York Metro
Top Internet Exchange Traffic Engines
- IX.br (Brazil)
- DE-CIX (Germany)
- AMS-IX (Netherlands)
- LINX (United Kingdom)
- JPNAP (Japan)
- HKIX (Hong Kong)
- SGIX (Singapore)
When activity resolves to unfamiliar locations, it’s often because traffic is passing through these shared hubs, the quiet middle layer of the internet that most people never see, but everyone depends on.






Leave a comment